
UDDI
Stands for "Universal Description Discovery and Integration." UDDI is a protocol that allows businesses to promote, use, and share services over the Internet. It is an OASIS Standard, which is supported by several major technology companies. Members include Microsoft, Cisco, Oracle, Avaya, Sun Microsystems, and others.
The UDDI protocol serves as a foundational tool that allows businesses to find each other and complete transactions quickly and easily. Companies that use the UDDI protocol can extend their market reach and find new customers while also finding other businesses that offer useful services to them. Because UDDI uses a standard format for describing business services, it is easy to search and find useful services offered from other businesses.
UDP
Stands for "User Datagram Protocol." It is part of the TCP/IP suite of protocols used for data transferring. UDP is a known as a "stateless" protocol, meaning it doesn't acknowledge that the packets being sent have been received. For this reason, the UDP protocol is typically used for streaming media. While you might see skips in video or hear some fuzz in audio clips, UDP transmission prevents the playback from stopping completely.
Ultra DMA
This technology for transferring data between a computer's hard disk and memory was developed by Quantum and Intel. The maximum burst rate of an Ultra DMA hard drive is 33.3 MBps. The original DMA (Direct Memory Access) protocol could only transfer data at half that speed.
Thanks to Ultra DMA, programs can open faster and run more smoothly. This is because Utlra DMA can send more data to the memory in less time than the original DMA. Ultra DMA also has a built-in utility called Cyclical Redundancy Checking (CRC) that helps protect data integrity. So if you want a nice, fast hard drive, look for one that supports Ultra DMA.
UML
Stands for "Unified Modeling Language." This is a programming language that is used for object-oriented software development. To organize program code more efficiently, programmers often create "objects" that are sets of structured data within programs. UML, which has been standardized by the Object Management Group (OMG), was designed for this purpose. The language has gained enough support that it has become a standard language for visualizing and constructing software programs.
UNC
Stands for "Universal Naming Convention," not just the home of the North Carolina Tar Heels. UNC is a filename format that is used to specify the location of files, folders, and resources on a local-area network (LAN). The UNC address of a file may look something like this:
\\server-name\directory\filename
UNC can also be used to identify peripheral devices shared on the network, including scanners and printers. It provides each shared resource with a unique address. This allows operating systems that support UNC (such as Windows) to access specific resources quickly and efficiently.
Unix
Also known as UNIX, though the letters do not stand for anything. The Unix operating system was first created in Bell Labs way back in the 1960s. It became popular in the 1970s for high-level computing, but not on the consumer level. Since a lot of Internet services were originally hosted on Unix machines, the platform gained tremendous popularity in the 1990s. It still leads the industry as the most common operating system for Web servers.
Still, Unix remains somewhat of an ambiguous operating system, as there are many different versions of it. Some examples include Ultrix, Xenix, Linux, and GNU, which, making things even more confusing, all run on a number of different hardware platforms. Most people do not ever need to use Unix, but computer geeks seem to have the need to use it as much as possible.
Unmount
Unmounting a disk makes it inaccessible by the computer. Of course, in order for a disk to be unmounted, it must first be mounted. When a disk is mounted, it is active and the computer can access its contents. Since unmounting a disk prevents the computer from accessing it, there is no risk of the disk being disconnected in the middle of a data transfer. Therefore, before removing an external data storage device, such as a USB flash drive, the disk should be unmounted to avoid possible data corruption.
Several types of disks can be unmounted, including external hard drives, USB flash drives, iPods, flash memory cards, and disk images. In order to unmount a disk in Windows, open "My Computer," select the disk, and click the "Eject this disk" option in the left sidebar. In Mac OS X, select the disk on the desktop and either drag the disk to the trash (which changes to an Eject icon), or select "File Eject" from the Finder's menu bar. Once a removable disk has been unmounted, it can safely be disconnected from the computer.
Upload
While downloading is receiving a file from another computer, uploading is the exact opposite. It is sending a file from your computer to another system. Pretty straight forward. It is possible to upload and download at the same time, but it may cause slower transfer speeds, especially if you have a low bandwidth connection. Because most files are located on Internet servers, people generally do a lot more downloading than uploading.
UPnP
Stands for "Universal Plug and Play." Plug and Play describes devices that work with a computer system as soon as they are connected. UPnP is an extension of this idea that expands the range of Plug and Play devices to networking equipment. Universal Plug and Play uses network protocols to allow a wide range of devices to be interconnected and work seamlessly with each other.
UPnP devices can be connected via wired (i.e. Ethernet and Firewire) or wireless (i.e. Wi-Fi and Bluetooth) connections. As long as a product supports UPnP, it can communicate with other UPnP devices within a network. The connections are typically created using the DHCP networking protocol, which assigns each connected device a unique IP address.
While UPnP is helpful for setting up networks, it also can be used to set up compatible audio and video (AV) devices. UPnP AV is a group of standards based on UPnP that allows audio and video components to be connected via network connections. This enables media files and streaming data to be sent between devices. For example, a movie stored on a hard drive in a bedroom could be played back on the TV screen in the living room. The central controller of a UPnP AV network is called a MediaServer and can be run from a Macintosh, Windows, or Linux computer or from a hardware device specifically designed to manage the network.
Since most UPnP devices support zero-configuration setup (like ordinary Plug and Play devices), it is simple to add devices to a network and use them immediately.
UPS
Stands for "Uninterruptible Power Supply." In the technology world, UPS is more than just a brown shipping company. It is also a type of power supply that uses battery backup to maintain power during unexpected power outages.

A typical consumer UPS is a surge protector that contains a high-capacity rechargeable battery. Smaller UPS devices look like bulky power strips, while larger ones may stand upright and look almost like small computers. Many businesses use uninterruptible power supplies to keep their equipment running in case of a power failure. While a UPS may only keep a computer running for 15 minutes after the power is lost, it is usually sufficient time to save all necessary documents and properly shut down the computer. That extra time can be invaluable to someone who is working on an important document or project that has not been recently saved.
Because UPS devices run the power through a battery, they have a limit on the wattage load they can support. The maximum power load limit is often included in the name of the UPS, followed by the letters "VA." For example, the APC (American Power Conversion) Battery Backup 750VA has a load limit of 750VA. However, the maximum wattage a UPS supports is typically 60% of the VA number. So the 750VA UPS supports a maximum of 450 watts for connected devices. It is important to check how many total watts your computer setup uses before buying a UPS to make sure you get one with enough wattage so you don't overload it.
URI
Stands for "Uniform Resource Identifier." A URI identifies the name and location of a file or resource in a uniform format. It includes a string of characters for the filename and may also contain the path to the directory of the file. URIs provide a standard way for resources to be accessed by other computers across a network or over the World Wide Web. They are used by software programs such as Web browsers and P2P file-sharing programs to locate and download files.
URIs are similar to URLs in that they specify the location of a file. However, a URI may refer to all or part a URL. For example, Apple's iMac Design URL is http://www.apple.com/imac/design.html. The URI of this resource may be defined as just "design.html" or "/imac/design.html." These are called relative URIs since they identify the resource relative to a specific location. The complete URL would be referred to as an absolute URI.
Because URLs and URIs are similar, they are often used interchangeably. In most cases, this is acceptable since the two terms often refer to the same thing. The difference is that a URI can be used to describe a file's name or location, or both, while a URL specifically defines a resource's location.
URL
Stands for "Uniform Resource Locator." A URL is the address of a specific Web site or file on the Internet. It cannot have spaces or certain other characters and uses forward slashes to denote different directories. Some examples of URLs are http://www.cnet.com/, http://web.mit.edu/, and ftp://info.apple.com/. As you can see, not all URLs begin with "http". The first part of a URL indicates what kind of resource it is addressing. Here is a list of the different resource prefixes:
http - a hypertext directory or document (such as a Web page)
ftp - a directory of files or an actual file available to download
gopher - a gopher document or menu
telnet - a Unix-based computer system that you can log into
news - a newsgroup
WAIS - a database or document on a Wide Area Information Search database
file - a file located on your hard drive or some other local drive
The second part of a URL (after the "://") contains the address of the computer being located as well as the path to the file. For example, in "http://www.cnet.com/Content/Reports/index.html," "www.cnet.com" is the address or domain name of the host computer and "/Content/Reports/index.html" is the path to the file. When a address ends with a slash and not something like ".html" or ".php," the Web server typically defaults to a file in the current directory named "index.html," "index.htm," or "index.php." So, if you type in "http://www.apple.com/" and "http://www.apple.com/index.html," you should get the same page.
USB
Stands for "Universal Serial Bus." USB is the most common type of computer port used in today's computers. It can be used to connect keyboards, mice, game controllers, printers, scanners, digital cameras, and removable media drives, just to name a few. With the help of a few USB hubs, you can connect up to 127 peripherals to a single USB port and use them all at once (though that would require quite a bit of dexterity).
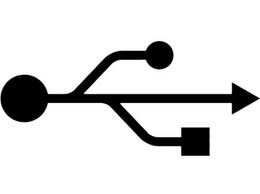

USB is also faster than older ports, such as serial and parallel ports. The USB 1.1 specification supports data transfer rates of up to 12Mb/sec and USB 2.0 has a maximum transfer rate of 480 Mbps. Though USB was introduced in 1997, the technology didn't really take off until the introduction of the Apple iMac (in late 1998) which used USB ports exclusively. It is somewhat ironic, considering USB was created and designed by Intel, Compaq, Digital, and IBM. Over the past few years, USB has become a widely-used cross-platform interface for both Macs and PCs.
User Interface
A user interface is the means in which a user controls a software program or hardware device. For example, a software interface may include windows, icons, menus, and buttons that allow the user to interact with the program. This is also known as a graphical user interface, or GUI. A hardware interface can be a remote control or a video game controller. It may also refer to the controls on a camcorder, digital camera, or iPod. Most modern user interfaces today are designed using a combination of hardware and software.
Utility
Utility programs, commonly referred to as just "utilities," are software programs that add functionality to your computer or help your computer perform better. These include antivirus, backup, disk repair, file management, security, and networking programs. Utilities can also be applications such as screensavers, font and icon tools, and desktop enhancements. Some utility programs help keep your computer free from unwanted software such as viruses or spyware, while others add functionality that allows you to customize your desktop and user interface. In general, programs that help make your computer better are considered utilities. And unlike water and electric bills, computer utilities don't send you a bill every month!
| Terms |
| UDDI |
| UDP |
| Ultra DMA |
| UML |
| UNC |
| Unix |
| Unmount |
| Upload |
| UPnP |
| UPS |
| URI |
| URL |
| USB |
| User Interface |
| Utility |
| Web Pages by Students |
ABC of C Language by Shailender Sharma |
Bootable Pen Drive by Avtar Singh |
e-Trash or e-Treasure? by Pallavi Bagga |
Lakshya by Rabina Bagga |
OOPs Concepts by Navjot Kaur |
Fitness First by Ankush Rathore |
Information Systems by Kajal Gupta |
Quiz Contest in C++ by Rajnish Kumar |
Core Java (Tutorial) by Shyena |
C Language Q&A by Anmol Sharma |
HTML 5 Tutorial by Kishan Verma |








