
Name Server
A name server translates domain names into IP addresses. This makes it possible for a user to access a website by typing in the domain name instead of the website's actual IP address. For example, when you type in "www.microsoft.com," the request gets sent to Microsoft's name server which returns the IP address of the Microsoft website.
Each domain name must have at least two name servers listed when the domain is registered. These name servers are commonly named ns1.servername.com and ns2.servername.com, where "servername" is the name of the server. The first server listed is the primary server, while the second is used as a backup server if the first server is not responding.
Name servers are a fundamental part of the Domain Name System (DNS). They allow websites to use domain names instead of IP addresses, which would be much harder to remember. In order to find out what a certain domain name's name servers are, you can use a WHOIS lookup tool.
NAT
Stands for "Network Address Translation." NAT translates the IP addresses of computers in a local network to a single IP address. This address is often used by the router that connects the computers to the Internet. The router can be connected to a DSL modem, cable modem, T1 line, or even a dial-up modem. When other computers on the Internet attempt to access computers within the local network, they only see the IP address of the router. This adds an extra level of security, since the router can be configured as a firewall, only allowing authorized systems to access the computers within the network.
Once a system from outside the network has been allowed to access a computer within the network, the IP address is then translated from the router's address to the computer's unique address. The address is found in a "NAT table" that defines the internal IP addresses of computers on the network. The NAT table also defines the global address seen by computers outside the network. Even though each computer within the local network has a specific IP address, external systems can only see one IP address when connecting to any of the computers within the network.
To simplify, network address translation makes computers outside the local area network (LAN) see only one IP address, while computers within the network can see each system's unique address. While this aids in network security, it also limits the number of IP addresses needed by companies and organizations. Using NAT, even large companies with thousands of computers can use a single IP address for connecting to the Internet. Now that's efficient.
Native File
When you save a file using a certain program, the file is often saved in a proprietary format only that program can recognize. For example, if you save a Microsoft Word document, it is saved as a Word document (i.e. mydocument.doc). This is a native Word file -- that is, the file format is native to the Microsoft Word application and may not be recognized by other programs.
When you use the "Save As..." command to save a file, you may be given the option to save the file in a different format. For example, you might be able to save a Word document as a plain text (.txt) file or a rich text (.rtf) file. These formats are not native to Microsoft Word, but can still be opened by the Microsoft Word program. Similarly, Adobe Photoshop saves files as Photoshop documents (.psd files), but can also save them in .jpg and .gif formats, among others.
It is usually best to save a file in a program's native file format because you can be sure it will store all the data you have created with the program. While other formats may be more compatible with other programs, they might not save all the information in the file. For example, if you save a Word document as a plain text file, all the text formatting you had added will be removed. Saving a Photoshop document in JPEG format will reduce the image quality and flatten all the image's layers.
So if you're planning on editing a file after you've saved it, saving it as a native file is the best choice. If you want to save the most compatible version of the file, saving a copy of the file in a more generic format is a good idea.
Netmask
A netmask is used to define a range of IP addresses. It is similar to a subnet mask, but is used to define classes of IPs rather than a range of IPs that may be used within a network. For example, IP addresses of class B have a subnet mask of 255.255.0.0. This means the IPs must all have the same first two sections, but may have different numbers for the second two sections.
Because a limited number of IP addresses are available, most IP ranges are assigned as Class C, which has a netmask 255.255.255.0. This defines a range of IPs that have identical numbers in the first three sections, but may contain any number between 0 and 255 in the final section. Therefore, a Class C netmask defines a range of 256 different addresses.
Example: "Class A IP addresses have a netmask of 255.0.0.0."
Network
When you have two or more computers connected to each other, you have a network. The purpose of a network is to enable the sharing of files and information between multiple systems. The Internet could be described as a global network of networks. Computer networks can be connected through cables, such as Ethernet cables or phone lines, or wirelessly, using wireless networking cards that send and receive data through the air.
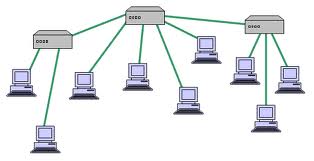
Network Topology
A network topology describes the arrangement of systems on a computer network. It defines how the computers, or nodes, within the network are arranged and connected to each other. Some common network topologies include star, ring, line, bus, and tree configurations. These topologies are defined below:
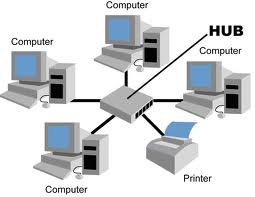
Star - One central note is connected to each of the other nodes on a network. Similar to a hub connected to the spokes in a wheel.
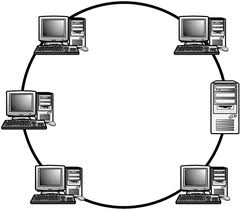
Ring - Each node is connected to exactly two other nodes, forming a ring. Can be visualized as a circular configuration. Requires at least three nodes.
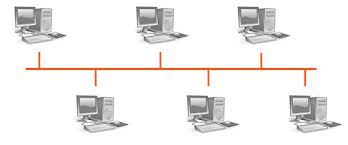
Bus - Nodes are arranged in a line, where most nodes are connected to two other nodes. However, the first and last node are not connected like they are in a ring.
Tree - One "root" node connects to other nodes, which in turn connect to other nodes, forming a tree structure. Information from the root node may have to pass through other nodes to reach the end nodes.
Newsgroup
A newsgroup is an Internet-based discussion about a particular topic. These topics range from sports, cars, investing, teen problems, and some stuff you probably don't want to know about. Users post messages to a news server which then sends them to a bunch of other participating servers. Then other users can access the newsgroup and read the postings. The groups can be either "moderated," where a person or group decides which postings will become part of the discussion, or "unmoderated," where everything posted is included in the discussion.
To participate in a newsgroup, you must subscribe to it. It typically doesn't cost anything, but some groups can be hard to get into unless you know people in the group. Nearly all newsgroups are found on Usenet, which is a collection of servers around the world. Because of the global spectrum of newsgroups, they make up largest bulletin board system (BBS) in the world. Last time I checked, there were more than 13,000 newsgroups in existence, with new ones being added all the time. You can choose from a number of different "Newsreader" programs that allow you to access and participate in newsgroups. Newsgroup access has also been integrated into Netscape and Internet Explorer, so you can just use your Web browser if you want.
NIC
Stands for "Network Interface Card." Pronounced "nick," this is the card that physically makes the connection between the computer and the network cable. These cards typically use an Ethernet connection and are available in 10, 100, and 1000 Base-T configurations. A 100 Base-T card can transfer data at 100 Mbps. The cards come in ISA and PCI versions and are made by companies like 3Com and LinkSys. So if you want to connect your computer to a network, you better get yourself a NIC.

NNTP
Stands for "Network News Transfer Protocol." For a message to be posted to a newsgroup, it must be sent through this protocol that interacts between news servers and newsreader programs. NNTP is basically the software foundation of a newsgroup server. It is what queries, distributes, posts, and retrieves news articles. Not too exciting, I know. But what do you expect -- this is computer terminology.
Node
Any system or device connected to a network is also called a node. For example, if a network connects a file server, five computers, and two printers, there are eight nodes on the network. Each device on the network has a network address, such as a MAC address, which uniquely identifies each device. This helps keep track of where data is being transferred to and from on the network.
A node can also refer to a leaf, which is a folder or file on your hard disk. In physics, a node, or nodal point, is a point of minimum displacement or where multiple waves converge, creating a net amplitude of zero.
Non-Impact Printer
Most modern printers are called non-impact printers since they do not operating by striking a print head against an ink ribbon. Two common types of non-impact printers include inkjet printers, which spray small drops of ink onto each page, and laser printers, which roll ink onto the paper using a cylindrical drum.
Non-impact printers are generally quieter and require less maintenance than impact printers, since they don't physically strike a ribbon against the paper. Of course, as we all know, modern printers can still find other ways not to work properly.
Example: "Inkjet and laser printers are common types of non-impact printers."
Northbridge
The northbridge is a chip inside a computer that connects the central processing unit (CPU) to other primary components in the system. These components include RAM (a.k.a. system memory), the frontside bus (FSB), PCI Express cards, and the AGP card. The northbridge also connects to the southbridge, which controls the remaining components of the computer.
While the CPU is the main processor inside the computer, the northbridge is the primary controller. It acts like a traffic cop directing data to and from the CPU. Therefore, the performance of the northbridge chip affects the overall performance of the computer. On Intel systems, the northbridge is also called the Memory Controller Hub (MCH), since it controls the data flow to and from the system memory.
NTFS
Stands for "New Technology File System." NTFS is a file system introduced by Microsoft with Windows NT and is supported by subsequent versions of Windows, such as Windows 2000 and Windows XP. NTFS has a number of advantages over the previous file system, named FAT32 (File Allocation Table). One major advantage of NTFS is that it includes features to improve reliablity. For exmaple, the new technology file system includes fault tolerance, which automatically repairs hard drive errors without displaying error messages. It also keeps detailed transaction logs, which tracks hard drive errors. This can help prevent hard disk failures and makes it possible to recover files if the hard drive does fail.
NTFS also allows permissions (such as read, write, and execute) to be set for individual directories and files. It even supports spanning volumes, which allows directories of files to be spread across multiple hard drives. The only reason why you would not want to select NTFS when formatting your hard drive is if you like slow, outdated technology or you need to run an older operating system such as Windows 95 or MS-DOS. Of course, if you are running DOS, there is a good chance you really do like outdated technology.
Null Character
A null character is a character with all its bits set to zero. Therefore, it has a numeric value of zero and can be used to represent the end of a string of characters, such as a word or phrase. This helps programmers determine the length of strings. In practical applications, such as database and spreadsheet programs, null characters are used as fillers for spaces.
Nybble
A nybble, sometimes spelled "nibble," is a set of four bits. Since there are eight bits in a byte, a nybble is half of one byte. While it may take the average person several nibbles to equal one bite of a cookie, in the computer world, two nybbles always equal one byte.
The four bits in a nibble allow it to have 16 possible values, which is the same as one hexadecimal digit. Therefore, a nybble is sometimes referred to as a "hex digit." In data communications, nybbles are sometimes called "quadbits," because of the four bits that make up each nybble.
| Terms |
| Name Server |
| NAT |
| Native File |
| Netmask |
| Network |
| Network Topology |
| Newsgroup |
| NIC |
| NNTP |
| Node |
| Non-Impact |
| Northbridge |
| NTFS |
| Null Character |
| Nybble |
| Web Pages by Students |
ABC of C Language by Shailender Sharma |
Bootable Pen Drive by Avtar Singh |
e-Trash or e-Treasure? by Pallavi Bagga |
Lakshya by Rabina Bagga |
OOPs Concepts by Navjot Kaur |
Fitness First by Ankush Rathore |
Information Systems by Kajal Gupta |
Quiz Contest in C++ by Rajnish Kumar |
Core Java (Tutorial) by Shyena |
C Language Q&A by Anmol Sharma |
HTML 5 Tutorial by Kishan Verma |








