
Tag
In Web pages, tags indicate what should be displayed on the screen when the page loads. Tags are the basic formatting tool used in HTML (hypertext markup language) and other markup languages, such as XML. For example, to create a table on a Web page, the <table> tag is used. The data that should be inside the table follows the <table> tag, and the table is closed with a </table> tag.
If you want something to show up in bold on a Web page, you would use the bold tag. For example, the line:
This site is the <b>best website</b> ever!
would show up as: This site is the best website ever!
<i> this is in italics</i>
would should up as: this is in italics
Tags are a fundemental part of HTML and they are pretty simple to understand. If you want to build a Web site of your own, you can either create it from scratch (using a text editor and typing your own tags) or you can use a layout program like Macromedia Dreamweaver, which will generate the tags for you.
Tape Drive
This is a removable storage device mainly used for backing up data. It is similar to a Zip Drive, but instead of Zip disks, it uses small tapes. The drive acts like a tape recorder, reading data from the computer and writing it onto the tape. Since tape drives have to scan through lots of tape to read small amounts of scattered data, they are not practical for most storage purposes. That is why they are used almost exclusively for data backup. The benefit of tape drives is that they typically have large capacities for storing data, for a lower cost than hard drives similar in size. Also, multiple tapes can be used to make incremental backups (daily, weekly, monthly, etc.), which is much cheaper than using multiple hard drives.
Target Disk Mode
Target disk mode is a way of booting a Macintosh computer so that it acts as an external hard drive on another computer. When a Mac is booted in target disk mode, the typical boot sequence is bypassed and the operating system is not loaded. Instead, the computer's internal and external hard drives are simply mounted on a connected computer. Target disk mode can be used to manually transfer files between two machines or to copy data from one computer to another using Apple's Migration Assistant.
In order for target disk mode (TDM) to work, two Macintosh computers must be attached to each other via a Firewire cable. One computer should be on and the computer designated for TDM should be off. To boot into target disk mode, hold the "T" key on the keyboard immediately after turning on or restarting the computer. After a few seconds, the screen should display the Firewire icon, which will move around the screen as long as the machine is in target disk mode. You should then see the hard drive(s) of the computer in TDM appear on the Desktop of the connected computer.
Booting a computer in target disk mode makes it easy to transfer files between two machines. Since the hard drives of the computer in TDM automatically mount on the other Mac's desktop, you can simply drag and drop files between them. Also, the computer in target disk mode is not seen as a boot disk, so you don't have to worry about file permissions. You can also run more comprehensive disk diagnostics and repairs. Just be sure not to remove or copy over any important system files on the TDM hard drive(s), since there are no safeguards to protect you from doing so.
Since the hard drives of the TDM machine are mounted on the connected computer, you should make sure to unmount or "eject" the hard drives before you turn off the computer. This can be done by selecting the hard drive on the desktop and choosing "Eject" from the File menu. Once the hard drives are ejected, you can safely turn off the TDM computer. When you turn on the computer again, it should boot normally (as long as you don't hold down the "T" key). Any files you copied to the computer's hard drives should appear in the directories you copied them to.
Task Bar
The task bar was introduced with Windows 95 and has been part of every version of Windows since then. It is the bar that spans the bottom of the screen and contains the Start button on the left side and the systray on the right. The task bar also includes the current time on the far right side and can hold shortcuts to programs directly to the right of the Start button.
Most of the task bar, however, contains shortcuts to open windows. Whenever you open a program or window, it shows up in the task bar. So if you have Internet Explorer and Microsoft Word open, there will be at least two items in the middle area of the task bar. Since each window gets its own location in the task bar, if there are two Microsoft Word documents open and three Internet Explorer windows open, there will be a total of five items in the task bar. When you click on a window title in the task bar, that window will become active and show up in front of other open windows. You can also cycle through the task bar items by holding the Alt key and pressing Tab a few times.
TCP/IP
Stands for "Transmission Control Protocol/Internet Protocol." These two protocols were developed in the early days of the Internet by the U.S. military. The purpose was to allow computers to communicate over long distance networks. The TCP part has to do with the verifying delivery of the packets. The IP part refers to the moving of data packets between nodes. TCP/IP has since then become the foundation of the Internet. Therefore, TCP/IP software is built into all major operating systems, such as Unix, Windows, and the Mac OS.
Tebibyte
A tebibyte is a unit of data storage that equals 2 to the 40th power, or 1,099,511,627,776 bytes.
While a terabyte can be estimated as 10^12 or 1,000,000,000,000 bytes, a tebibyte is exactly 1,099,511,627,776 bytes. This is to avoid the ambiguity associated with the size of terabytes. A tebibyte is 1,024 gibibytes and precedes the pebibyte unit of measurement.
Telnet
This is a program that allows you log in to a Unix computer via a text-based interface. If you have an account on a Telnet server, you can access certain resources on the system such your home directory, your e-mail account, FTP files, etc. The downside of Telnet is that, to use it, you need to use Unix commands, which can be a challenge.
Template
A template is a file that serves as a starting point for a new document. When you open a template, it is pre-formatted in some way. For example, you might use template in Microsoft Word that is formatted as a business letter. The template would likely have a space for your name and address in the upper left corner, an area for the recipient's address a little below that on the left site, an area for the message body below that, and a spot for your signature at the bottom.
When you save a file created with a template, you are usually prompted to save a copy of the file, so that you don't save over the template. Templates can either come with a program or be created by the user. Most major programs support templates, so if you find yourself creating similar documents over and over again, it might be a good idea to save one of them as a template. Then you won't have to format your documents each time you want to make a new one. Just open the template and start from there.
Terabyte
A terabyte is 2 to the 40th power, or 1,099,511,627,776 bytes.
It can be estimated as 10 to the 12th power, or 1,000,000,000,000 bytes. A terabyte is 1,024 gigabytes and precedes the petabyte unit of measurement. While today's consumer hard drives are typically measured in gigabytes, Web servers and file servers may have several terabytes of space. A single 500GB hard drive can also be called a half-terabyte drive.
The prefix "tera" comes from the Greek word meaning "monster." So, if you have a 500GB hard drive, you could say you have half a monsterbyte of disk space. If nothing else, it sure sounds impressive.
Teraflops
Teraflops (also TFLOPS) is used to measure the performance of a computer's floating point unit (FPU). One teraflops equals 1,000 gigaflops, or 1,000,000,000,000 FLOPS. The term "teraflops" may be singular or plural because FLOPS is short for "Floating Point Operations Per Second." Teraflops is often used to measure scientific computing performance, since most scientific calculations use floating point operations.
Example: "Supercomputing performance is often measured in teraflops."
Terminal
The word "terminal" comes from early computer systems that were used to send commands to other computers. Terminals often consist of just a keyboard and monitor, with a connection to another computer. The purpose of a terminal is not to process information (like a typical computer), but to send commands to another system. For example, a network administrator may use a terminal to log in to a network and manage devices connected to the network.
With modern computers, the word "terminal" usually refers to a terminal program, or emulator, which provides a text-based interface for typing commands. This type of program is often abbreviated "TTY" and may also be referred to as a command-line interface. Terminal programs are available for all major computing platforms and are typically included with the operating system. For example, Mac OS X includes a program appropriately called "Terminal," which can be used to run Unix commands within the Mac OS or to access other machines. Unix typically includes a program called "xterm," which can run BASH or other Unix shells.
Unlike most modern computer programs, terminal emulators do not have very user-friendly interfaces. In order to use a terminal program effectively, you need to know Unix (or DOS) commands. Typing "help" or "man" may provide you with an overview of commands, though it can be difficult to use them if you don't know what parameters to include with each command. This Unix Commands Reference may be helpful if you are using a Unix terminal for the first time.
Text Editor
A text editor is any word processing program that you can use to type and edit text. Hey, they don't call it a text editor for nothing... Word Pad and NotePad for Windows and SimpleText and TextEdit for the Mac are common text editors. Larger programs such as Microsoft Word and Word Perfect are also text editors, but they have many more features. You can actually write HTML code and create HTML pages with a simple text editor, as long as you know the correct HTML syntax.
TFT
Stands for "Thin Film Transistor." These transistors are used in high-quality flat panel liquid-crystal displays (LCDs). TFT-based displays have a transistor for each pixel on the screen. This allows the electrical current that illuminates the display to be turned on and off at a faster rate, which makes the display brighter and shows motion smoother. LCDs that use TFT technology are called "active-matrix" displays, which are higher-quality than older "passive-matrix" displays. So if you ever see a TFTAMLCD monitor at your local computer store, it is a "thin-film transistor active-matrix liquid crystal display." Basically, it is a high-quality flat screen monitor.
Thick Client
Thick clients, also called heavy clients, are full-featured computers that are connected to a network. Unlike thin clients, which lack hard drives and other features, thick clients are functional whether they are connected to a network or not.
While a thick client is fully functional without a network connection, it is only a "client" when it is connected to a server. The server may provide the thick client with programs and files that are not stored on the local machine's hard drive. It is not uncommon for workplaces to provide thick clients to their employees. This enables them to access files on a local server or use the computers offline. When a thick client is disconnected from the network, it is often referred to as a workstation.
Third Party
Third party software refers to software programs developed by companies other than the operating system developer. It may also refer to third party plug-ins, which are developed by other companies besides the original application developer.
Third party hardware refers to computer equipment manufactured by companies other than the original manufacturer. Examples of third party components include hard drives, video cards, memory modules, and peripheral devices.
Thread
What do a t-shirt and a computer program have in common? They are both composed of many threads! While the threads in a t-shirt hold the shirt together, the threads of a computer program alllow the program to execute sequential actions or many actions at once. Each thread in a program identifies a process that runs when the program asks it to (unlike when you ask your roommate to do the dishes).
Threads are typically given a certain priority, meaning some threads take precedence over others. Once the CPU is finished processing one thread, it can run the next thread waiting in line. However, it's not like the thread has to wait in line at the checkout counter at Target the Saturday before Christmas. Threads seldom have to wait more than a few milliseconds before they run. Computer programs that implement "multi-threading" can execute multiple threads at once. Most modern operating systems support multi-threading at the system level, meaning when one program tries to take up all your CPU resources, you can still switch to other programs and force the CPU-hogging program to share the processor a little bit.
The term "thread" can also refer to a series of related postings in an online discussion. Web-based bulletin boards are made up of many topics, or threads. The replies posted in response to the original posting are all part of the same thread. In e-mail, a thread can refer to a series of replies back and forth pertaining a certain message.
Throughput
Throughput refers to how much data can be transferred from one location to another in a given amount of time. It is used to measure the performance of hard drives and RAM, as well as Internet and network connections.
For example, a hard drive that has a maximum transfer rate of 100 Mbps has twice the throughput of a drive that can only transfer data at 50 Mbps. Similarly, a 54 Mbps wireless connection has roughly 5 times as much throughput as a 11 Mbps connection. However, the actual data transfer speed may be limited by other factors such as the Internet connection speed and other network traffic. Therefore, it is good to remember that the maximum throughput of a device or network may be significantly higher than the actual throughput achieved in everyday use.
Thumbnail
A thumbnail is the nail on your thumb. If you look at your thumbnail, you will notice it is rather small in size. This is why the term "thumbnail" is also used to refer to a reduced size version of a digital image. While digital thumbnails might not always be as small as a human thumbnail, they are usually less than 200x200 pixels in size.
Thumbnails, or thumbnail images, are often used on the Web and in digital photo organization programs. Because of their small size, several thumbnails can be displayed on a single screen. This makes it possible to browse through several images at once. In most instances, clicking or double-clicking on a thumbnail will open the full size image.
TIFF
Stands for "Tagged Image File Format." It is graphics file format created in the 1980's to be the standard image format across multiple computer platforms. The TIFF format can handle color depths ranging from 1-bit to 24-bit. Since the original TIFF standard was introduced, people have been making many small improvements to the format, so there are now around 50 variations of the TIFF format. So much for a universal format. Recently, JPEG has become the most popular universal format, because of its small file size and Internet compatibility.
Toggle Key
A toggle key is used to alternate the input mode of a group of keys on a keyboard. Some examples include Caps Lock, Insert, Num Lock, and Scroll Lock. Caps Lock is the most commonly used toggle key, and capitalizes all letter input when turned on. The Insert key toggles the text entry mode between insert (which inserts characters) and overtype (which overwrites characters). Num Lock makes sure numbers are input from the numeric keypad and Scroll Lock allows the arrow keys to scroll through the contents of a window.
All keyboards include the Caps Lock key and most keyboards include Num Lock. The Insert and Scroll Lock keys are found on many keyboards as well, but they are rarely used an not supported by all operating systems.
Example: "The Caps Lock toggle key capitalizes letters typed on a keyboard."
Token
A token is a group of bits that are transferred between computers on a token-ring network. Whichever computer has the token can send data to the other systems on the network. This ensures that only one computer can send data at a time.
A token may also refer to a network security card, also known as a hard token.
Example: "Computers on a token-ring network can only send data when they have the token."
Tooltip
As computer users, we have become accustomed to icons that represent files, folders, programs, and other objects on the computer. Many software programs also use icons to represent tools, which are often found in the program's toolbar.
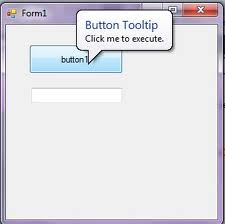
While these icons can save screen space and make the program's interface more attractive, it can sometimes be difficult to tell what all the tool icons mean. While some tool icons are obvious (such as a printer icon to print and a scissors icon to cut a text selection), others are a bit more ambiguous. For this reason, programs often include tooltips that explain what each tool icon represents.
Tooltips are displayed when you roll over an icon with the cursor. It may take a second or two to display the tooltip, but when it does appear, it usually is a small box with a yellow background explaining what the icon represents. For example, in Microsoft Word, when you roll over the disk icon, the tooltip "Save" appears. This means clicking on the disk icon will save your document. In Photoshop, when you roll over the wand icon, the text "Magic Wand Tool (W)" appears. This indicates that clicking the the wand icon or pressing the W key will activate the magic wand selection tool.
Not all programs incorporate tooltips, but most modern programs include them as part of a user-friendly interface. Operating systems also support them in different ways. For example, Mac OS X will show the full text of a long filename when you place the cursor over the filename. Windows includes tooltips for the systray icons and also tells you information about each file and folder you place the cursor over. If you drag your cursor over different icons on your computer, you may find tooltips you never knew were there!
Torrent
A torrent is a file sent via the BitTorrent protocol. It can be just about any type of file, such as a movie, song, game, or application. During the transmission, the file is incomplete and therefore is referred to as a torrent. Torrent downloads that have been paused or stopped cannot be opened as regular files, since they do not contain all the necessary data. However, they can often be resumed using a BitTorrent client, as long as the file is available from another server.
Torrents are different from regular downloads in that they are usually downloaded from more than one server at a time. The BitTorrent protocol uses multiple computers to transfer a single file, thereby reducing the bandwidth required by each server. When a torrent download is started, the BitTorrent system locates multiple computers with the file and downloads different parts of the file from each computer. Likewise, when sending a torrent, the server may send the file to multiple computers before it reaches the recipient. The result is a lower average bandwidth usage, which speeds up file transfers.
Traceroute
When computers communicate over the Internet, there are often many connections made along the way. This is because the Internet is made up of a network of networks, and two different computers may be on two separate networks in different parts of the world. Therefore, if a computer is to communicate with another system on the Internet, it must send data through a series of small networks, eventually getting to the Internet backbone, and then again traveling to a smaller network where the destination computer resides.
These individual network connections, called "hops," typically go unnoticed by the average user. After all, why bother tracking all the various connections when you are only interested in communicating with the destination computer? However, if a connection cannot be made or is taking a unusually long time, tracing the path of connections along the way can prove to be helpful. This is exactly what the traceroute command does.
Traceroute is a TCP/IP utility that allows a user to trace a network connection from one location to another, recording every hop along the way. The command can be run from a Unix or DOS command line by typing tracert [domain name], where [domain name] is either the domain name or the IP address of the system you are trying to reach. A traceroute can also be done using various networking utilities, such as Apple's Network Utility for Mac OS X.
When a traceroute is run, it returns a list of network hops and displays the host name and IP address of each connection. It also returns the amount of time it took for each connection to take place (usually in milliseconds). This shows if there were any delays in establishing the connection. Therefore, if a network connection is slow or unresponsive, a traceroute can often explain why the problem exists and also show the location of the problem.
Trackball
A trackball is an input device that has a ball which is held in a socket and can be rolled in any direction. Most trackballs perform the same functions as a mouse and are used primarily to control the cursor on a computer screen. However, unlike a mouse, a trackball device remains stationary when the user move the ball. This makes trackballs ideal for areas with limited space.
Trash
The Trash is used by Macintosh computers to store deleted items. It serves as a safety net, which provides an extra step before items are permanently deleted from the computer. Items can be moved to the Trash by dragging them to the Trash icon in the Dock or by selecting them and pressing Command-Delete.

You can view the items in the Trash by clicking the Trash icon. If you wish to save any of the items, you can drag them out of the Trash folder. If you are sure you no longer need the items in the Trash, you can select "Empty Trash..." from the Finder menu. This will permanently delete all the items stored in the Trash and will free up the disk space the items had been using.
Trojan Horse
In Greek mythology, there is a story about the Trojan War. This war lasted many years, as the Greeks could not penetrate the heavily barricaded city of Troy. So one day, a few of the Greek soldiers brought the people of Troy a large wooden horse, which they accepted as a peace offering. The horse was moved inside the city walls, where it sat until the night. After the people of the city had fallen asleep, Greek soldiers jumped out of the wooden horse, opened the gates to let their fellow soldiers in, and took over the city.
So what is the moral of this story? Mainly, beware of Trojan horses. But how does that relate to computers? That's a good question. In the computing world, Trojan horses are more than just a myth. They really exist and can cause damage to your computer. Trojan horses are software programs that masquerade as regular programs, such as games, disk utilities, and even antivirus programs. But if they are run, these programs can do malicious things to your computer.
For example, a Trojan horse might appear to be a computer game, but once you double-click it, the program starts writing over certain parts of your hard drive, corrupting your data. While this is certainly something you want to avoid, it is good to know that these malicious programs are only dangerous if they are given a chance to run. Also, most antivirus programs can catch Trojan horses when scanning for viruses. Unlike viruses, however, Trojan horses don't replicate themselves. Though it is possible for a Trojan horse to be attached to a virus file that spreads to multiple computers.
So as a general rule, don't open a program unless you know it is legitimate. This applies especially to e-mail attachments that are executable files. Even if you are pretty sure the attachment is OK, it is still a good idea to run it through your virus scan program (with the latest virus definitions) just to be safe. Remember what happened to the people of Troy -- don't let a Trojan horse catch you off guard.
Troubleshooting
Troubleshooting is the process or identifying and fixing problems. Computer troubleshooting may involve hardware or software and can sometimes involve both at the same time. The basic process of troubleshooting is to check the most general possible problems first, and then gradually check for more specific problems. This provides a logical approach to problem solving and can apply to multiple types of products.
Truncate
To truncate something is to shorten it, or cut part of it off. In computer science, the term is often used in reference to data types or variables, such as floating point numbers and strings.
For example, a function may truncate the decimal portion of a floating point number to make it an integer. If the number 3.875 is truncated, it becomes 3. Note that this is different than if the number had been rounded to the nearest integer, which would be 4. Strings may also be truncated, which can be useful if a string exceeds the maximum character limit for a certain application.
Several programming languages use the function trunc() to truncate a variable. PHP uses strlen() to truncate a string to a set limit of characters.
Tweak
When you modify a certain piece of hardware for better performance, it is often referred to as "tweaking" it. Overclocking the computer's CPU or changing jumper settings on the motherboard are common examples of hardware tweaking. Removing system limitations and adding plug-ins or extensions to a computer's operating system are types of software tweaking.
Tweaking a computer is much like "tuning" a car (you know, the ones with the huge mufflers, big spoilers, and pimped out rims). It may increase performance, but is best left in the hands of the technically savvy. For example, overclocking your computer's processor may cause it to crash frequently, or worse yet, overheat and destroy the CPU. So, for most people, it is best to leave well enough alone.
Tweet
A tweet is an update published by a Twitter user. It is similar to a blog posting, but cannot be longer than 140 characters. Tweets are meant to answer the question, "What are you doing?" which provides other users with quick updates about your life. When you publish a tweet, it will show up on the Twitter home pages of all the users you are following. Similarly, when you log in to Twitter, you will see the most recent tweets of the users that you have chosen to follow.
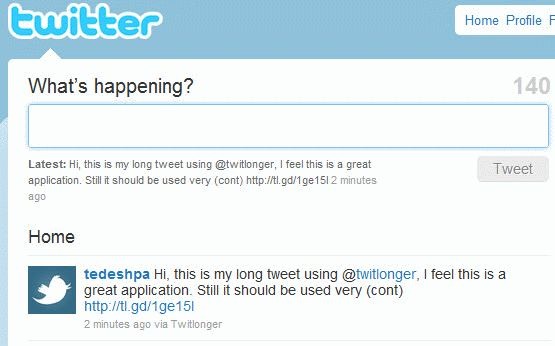
Twitter is a service that allows people to stay connected with each other by answering the basic question, "What are you doing?" Once you sign up for a Twitter account, you can post your own updates, or "tweets," using a computer or cell phone. You can also view the updates posted by other users you are following. Since each tweet is limited to 140 characters or less, the updates must be short and sweet. However, you may twitter as often as you want, meaning there is no limit on how much information you can share.

Typeface
A typeface is a set of characters of the same design. These characters include letters, numbers, punctuation marks, and symbols. Some popular typefaces include Arial, Helvetica, Times, and Verdana. While most computers come with a few dozen typefaces installed, there are thousands of typefaces available. Because they are vector-based (not bitmaps), typefaces can be scaled very large and still look sharp. The term "typeface" is often confused with "font," which is a specific size and style of a typeface. For example, Verdana is a typeface, while Verdana 10 pt bold is a font. It's a small difference, but is good to know.
| Web Pages by Students |
ABC of C Language by Shailender Sharma |
Bootable Pen Drive by Avtar Singh |
e-Trash or e-Treasure? by Pallavi Bagga |
Lakshya by Rabina Bagga |
OOPs Concepts by Navjot Kaur |
Fitness First by Ankush Rathore |
Information Systems by Kajal Gupta |
Quiz Contest in C++ by Rajnish Kumar |
Core Java (Tutorial) by Shyena |
C Language Q&A by Anmol Sharma |
HTML 5 Tutorial by Kishan Verma |








